The scope of this Solution is not the installation of Remedy Single Sign-On, the scope of the Solution is to integrate a installed Remedy Sing--On environment into Active Directory Using LDAP protocol.
This Solution does cover the following chapters:
- Prerequisites
- What configuration settings can be re-used from a ASSO - LDAP integration
- Overview for settings and parameter used for the integration
- Troubleshooting and find the correct Distinguished Name Search path for User and Groups
- Prerequisites
1. Installed version of RSSO supported by TrueSight 11 family
2. If possible a TrueSight Presentation Server integrated into RSSO ( useful to validate the LDAP integration)
The best in-house source to get the information below is the Windows Domain Administrator team.
3. Domain Controller Hostname with low network latency used for the LDAP connection.
If possible a Domain Controller in the same sub-net or at least same region.
Consider to connect to a Global Catalog, for large forest Active Directory and site and Universal Groups.
If you don't know the hostname of a domain controller you can run nslookup command against the domain name on a Windows PC.
For example "nslookup domain.com"
4. Does Active Directory support LDAPS (LDAP over SSL)?
This connection is using port 636, it is recommended because all communication is encrypted, typically a Windows Enterprise Certificate Authority is used.
If not possible LDAP using port 389 has to be used, communication is not encrypted, unless encryption is established with VPN or Layer 2 or 3 security.
If LDAPS against Port 636 or 3269 for the Global Catalog is used, it is required to get a certificate from all the domain controllers to connect.Or preferable a single certificate from the enterprise certificate authority which signs the domain controller certificates, this certificate is typically valid for a longer time also.
See troubleshooting chapter at the end of the document how to import the certificate by using keytool
5. Bind DN - User Account in Distinguished Name Format with Password which is used for the initial LDAP Bind as a service account.
Consider if a Domain Policy requires password changes for the account, the password has to be in sync at the RSSO configuration.
The same account and password can be used as for Atrium Single Sign-On.
6. User Base DN:
The Distinguished Name from the Orgainzation Unit Structure under which all User can be found, in fact the Root DN of the Domain can be used.
For performance and security reasons it is recommended to use a DN which is more down in the Organization Unit hierarchy
7. Group Base DN:
The same as for Users, the Groups can be stored in a different Organization Unit structure
For performance and security reason is is recommended to find a DN under which all groups required for authorization can be found.
8. Group Filter for Search:
Get the name of the groups supposed to login into TrueSight products for authentication.
In a large Active Directory requirement it is recommended to setup Filter to only search for the required groups.
Without proper group filter the authentication process can be slow, or the queries results from RSSO against Active Directory exceeding the number of results limited by Active Directory which may prevent that logins are not working at all. A few examples for Group Filter are at the end of the Overview chapter.
- What configuration settings can be re-used from a ASSO - LDAP integration.
| ASSO | RSSO |
|---|
| Realm Authentication, Primary LDAP Server, Name | Realm Authentication,LDAP Authentication, Server Host |
| Realm Authentication, Primary LDAP Server, Port | Realm Authentication,LDAP Authentication, Server Port |
| Realm Authentication,User Account for Search, User Account for Search | Realm Authentication,LDAP Authentication, Bind DN |
| Realm Authentication,User Account for Search, Password | Realm Authentication,LDAP Authentication, Bind Password |
| Realm Authentication, DN to Start Search, Base DN | Realm Authentication,LDAP Authentication, Users Base DN |
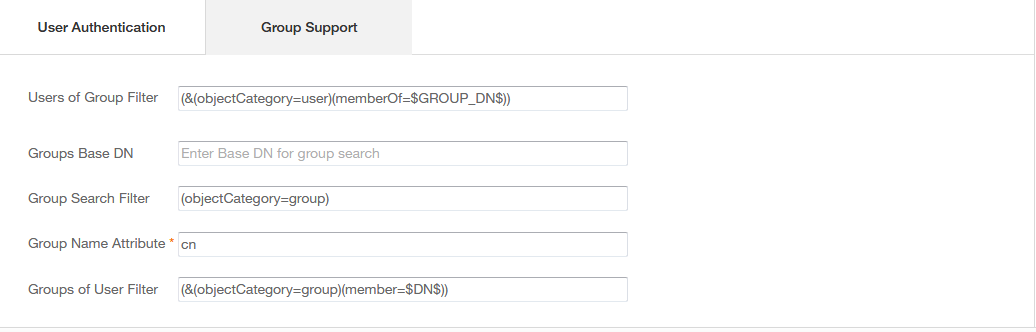
| LDAP Users Store, Search Tab, Search Base DN | Realm Authentication,LDAP Authentication, Group Support, Group Base DN |
- Overview for settings and parameter used for the integration
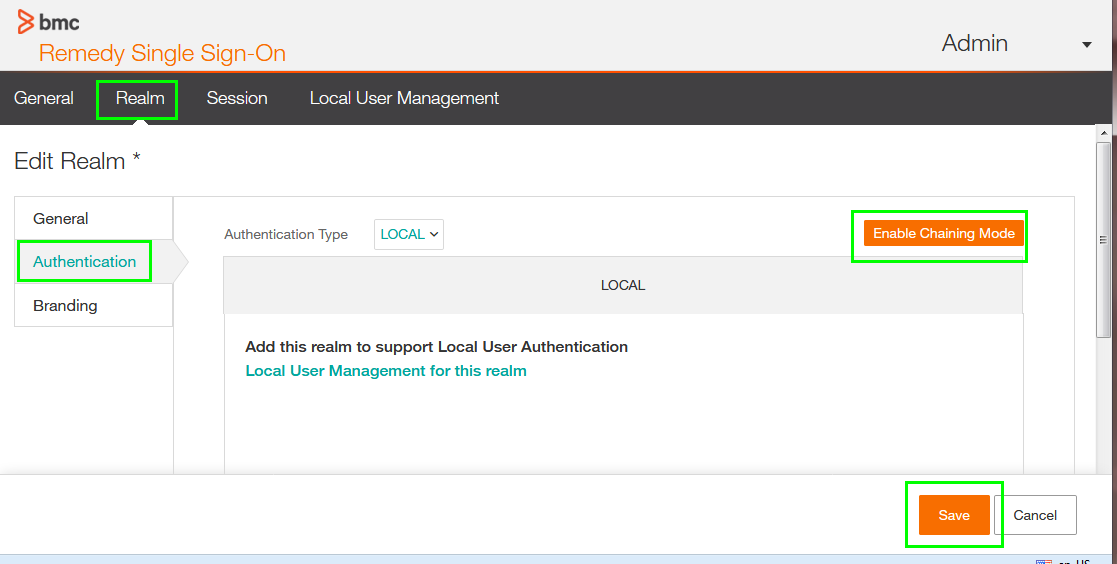
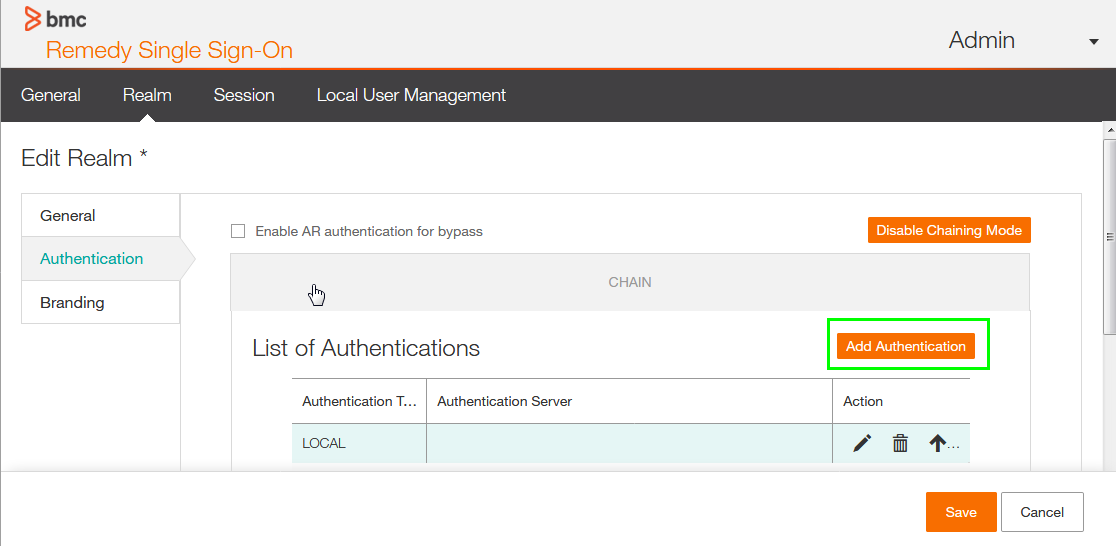
1. Login to RSSO navigate to Realm open the default Realm * in Edit mode, select Authentication and Enable Chaining Mode, this allows to use Local and a second external authentication, save changes.
Note: When using multiple authentication modes, the first on the list is picked up first, If the same user does exit in multiple stores the first is researched first. With multiple authentication types a typical order would be. Kerberos > LDAP > LOCAL. Which would mean that users in the local store are picked up as the last option. If RSSO is integrated into Kerberos it should always the top of the list.
RSSO configuration changes require the local Admin user, this configuration changes are not possible with remote users, the default password is RSSO#Admin#.
To change the default password, you can use the Admin drop down list in the right upper corner.
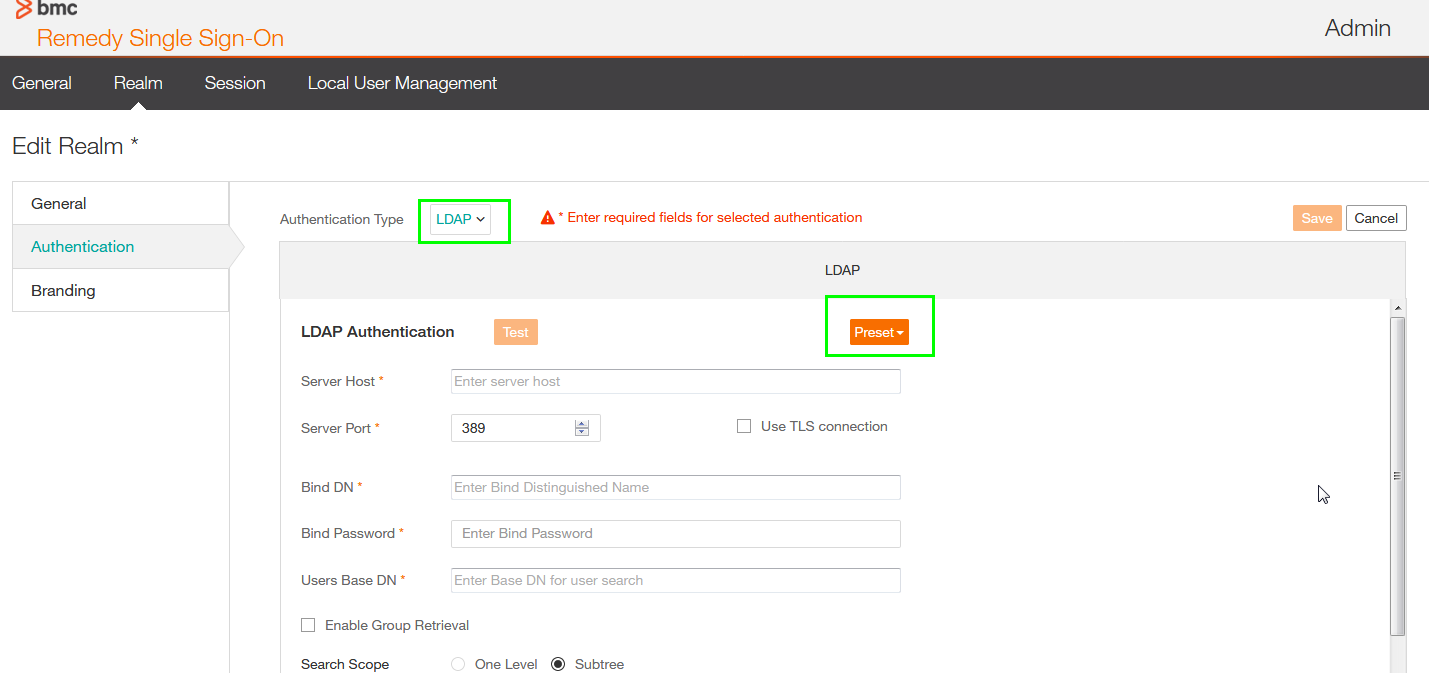

- Verify that Enable Group Retrieval is enabled and the Search Scope is Subtree, without the later RSSO only looks to this Organization Unit defined as User Search DN.
- With the Subtree option enabled RSSO search recursively ( ldap referral) does in the Organization Unit structure.
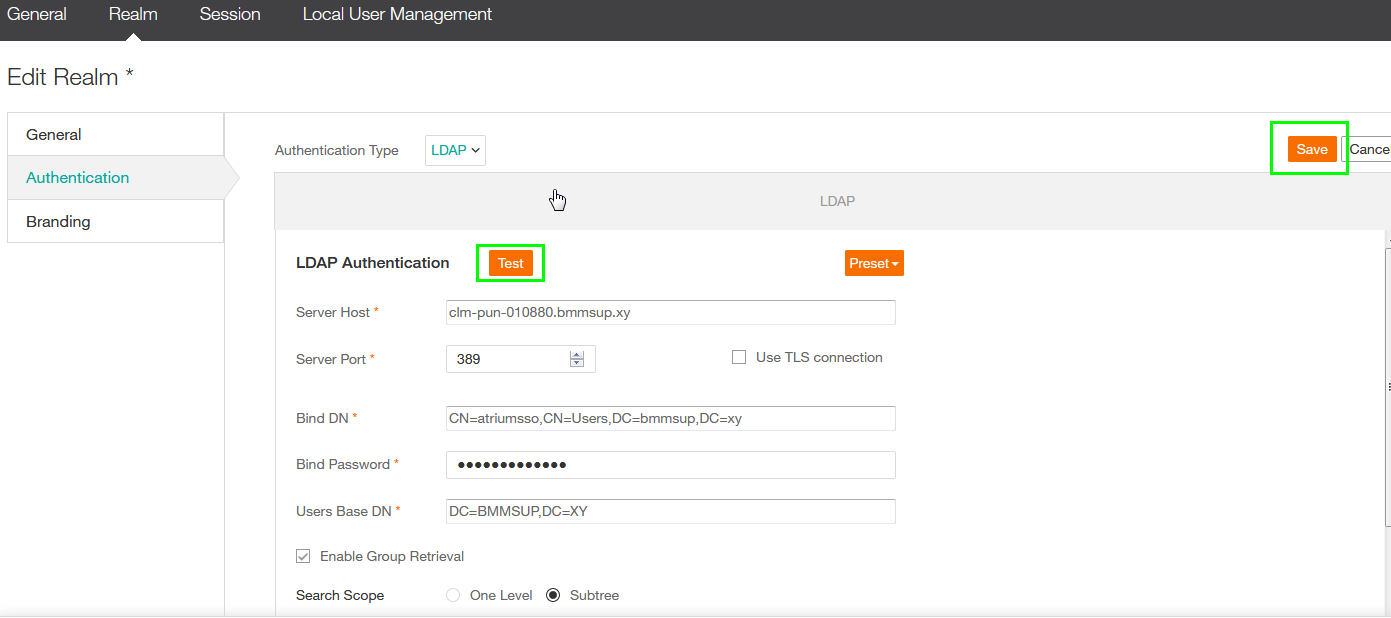
- Use the Test button, if the Test completed with OK, RSSO can connect with the Domain Controller.
- Consider to use Port 636 is LDAPS is available and don't forget to enable the "The Use TLS connection" checkbox.
But TLS secured communication requires that you import the certificate from the domain controllers, or better from the certificate authority which signs the certificate.
See the keytool example in this document how you can import a certificate.
- If unsure about the Users Base DN, see troubleshooting section.
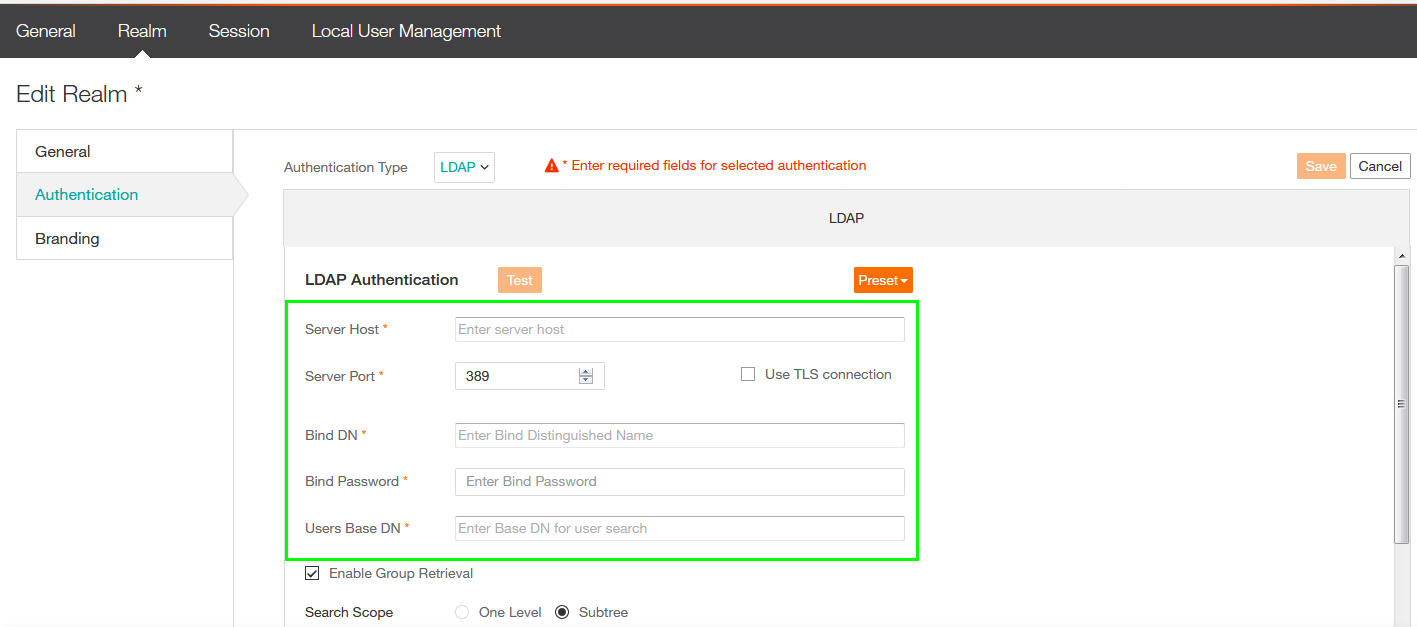
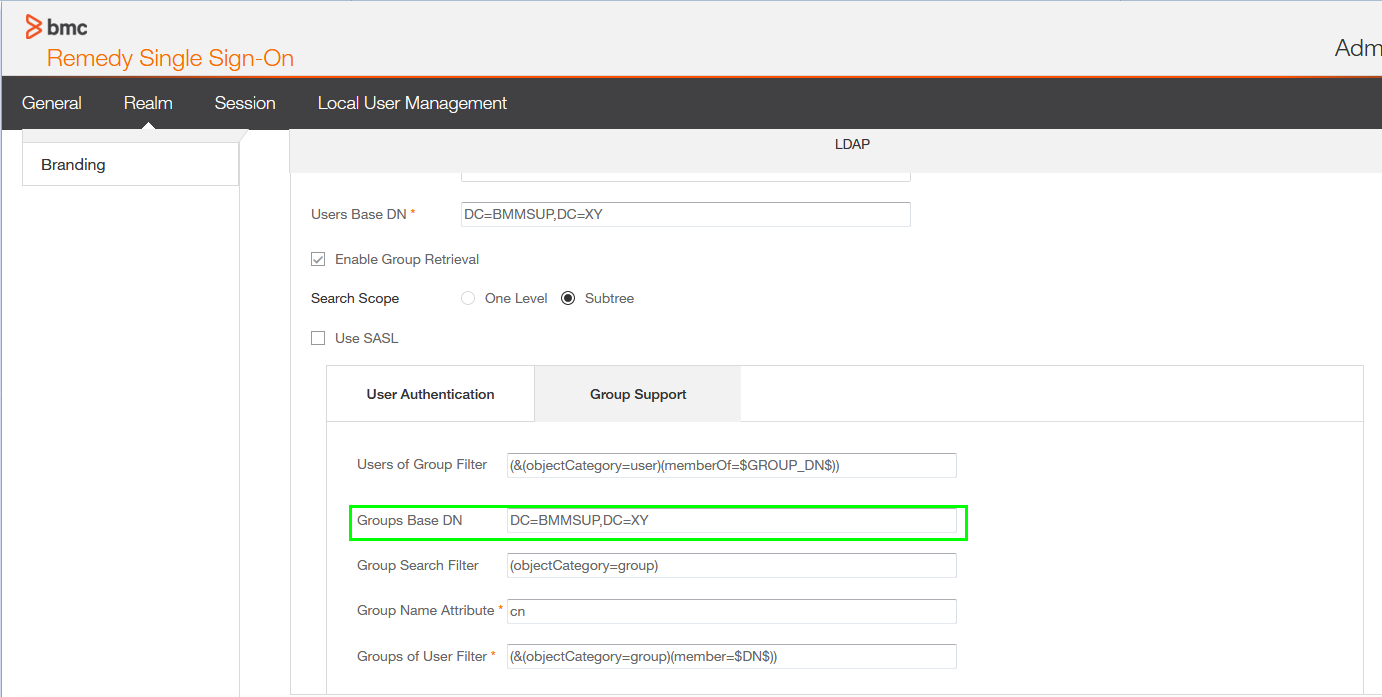
In this screenshot you may realize that the root of the Domain is used as Users Base DN and Groups Base DN, this is typically not recommended.
But might be required if the Users and Groups are already in different top level OUs.
For example users and groups exist in each of the Organization Units OU=BMM,DC=BMMSUP,DC=XY and OU=TSCO,DC=BMMSUP,DC=XY and every user of this groups needs to login.
into the TrueSight products The root of the domain is needed as well if you have users in child domain using the same domain tree.
If you use a top level or high level structure in the Active Directory domain , you must setup proper group filter. If not logins take long time, or are even not possible and may show in the<RSSO_Install>/rsso/tomcat/logs/rsso.0.log: ERROR: [LDAP: error code 4 - Sizelimit Exceeded]
Which means that the result received by LDAP from RSSO is larger as the allowed limit, which is typically 1000 results.
See being of the troubleshooting sections how to use Group Filter and How to evaluate the best DNs for Users and Groups.
- Troubleshooting - LDAP Group Filter - LDAPS(SSL) - find the right DN- testing by using TSPS
You cannot use the RSSO Gui to determine if the LDAP integration is working fine, you can verify the settings used outside RSSO for example by using TSPS and you can check the log.
There is no way to display or manage users from a remote Realm authentication, RSSO does only support the management of local users and groups.
Log:
Errors related with the LDAP connections are written to the $RSSO_HOME/rsso/tomcat/logs/rsso.0.log:
LDAP Filter
The filter are very important, because you can filter out for groups, you can filter out to only use security groups and you can filter out for persons instead of users.
A detailed documentation for LDAP can be found on the Microsoft Technet Pages under this URL.
https://social.technet.microsoft.com/wiki/contents/articles/5392.active-directory-ldap-syntax-filters.aspx
a:) Filter out for groups Group search Filter to filter out for 2 groups with the cn BMM and TSCO you can simple change the filter from
(objectCategory=group) to:
(&(objectCategory=group)(|(cn=BMM)(cn=TSCO)))
This would only process this group names, the filter example for more groups works in this way:
(&(objectCategory=group)(|(cn=GroupA)(cn:=GroupB)(cn=GroupC)(cn=GroupD)(cn=GroupN)))
b:) Filter out for groups with regular expression, for example all groups with a prefix Group are supposed to login into TrueSight, makes the filter shorter.
(&(objectCategory=group)(cn=Group*))
LDAPS SSL integration issue
When trying to connect to an LDAP port 636 instead of 389 or 3269 instead of 3268 for the Global Catalog, the GUI is showing this error:
SSL certificate is missing or port is incorrect
Please double check with the Windows Active Directory Administrator if LDAPS is supported and configured to the port used in the attempt generated this error.
If so, request a certificate from the certificate authority which has signed the certificate for the Domain Controller, it is very likely an Enterprise Certificate Authority, or a Root Certificate Authority.
Get this certificate if possible in Base 64 format and transfer the file in binary format to the RRSO server, to import this certificate.
- navigate with command line to the $RSSO_HOME/rsso/jre/bin directory
Important: RSSO has 2 JRE directories: RSSO_HOME/rsso/jre and RSSO_HOME/jre/
It is required to import the certificates to the $RSSO_HOME/rsso/jre/lib/security/cacerts truststore file importing the certifcates into $RSSO_HOME/jre/lib/security/cacerts does not help.
- run keytool in this way.
./keytool -alias root -import -keystore ../lib/security/cacerts -trustcacerts -file /full/path/to/certificate.cer
The default password of the cacerts file is changeit, please be aware that the cacerts file is overwritten when doing a product update.
To change this password and use a custom truststore is not the scope of this Solution, if this is required please open a case with support.
The alias parameter can be used as a free form, it must be unique, but you can use the name of the CA signed the certificate.
Find the best Search DN
The best DN depends on the Active Directory Organization Unit Structure and is quite unique for every environment.
If users from child domains are supposed to login in the same domain tree, for example domain.com and child.domain.com, it is required to use the Root DN of the root domain
for the User and and Group Search DN, please consider to use Group Filter when using this approach.
For domains in the same forest, but different domain tree like domain.com and domain.co.uk, or with domains using a trust relationship you need separate LDAP Authorization for each.
Because this domains have different root DN and the DN must match, accross the domain for this kind of recommendations.
On method to find the right DN is using a common LDAP Explorer, however this may take a long time to understand the structure, and it may cause confusion if the domain has user and computer objects with the same name.
An easier method is to use dsquery and dsget commands, this commands are available on a Domain Controller, or on boxes where the Active Directory client tools are installed.
So it might be required to ask a Administrator to run the command, this may take some time , but during that time you can work on other integration issues.
The advantage is that this command examples provide the output you need to find the best DN in a good and readable format.
1. Get the DN of all member of a Group, replace groupname with the name of the group
dsquery group -name groupname | dsget group -members -expand
a. example output
CN=user1,OU=IT,OU=US,DC=DOMAIN,DC=COM
CN=user2,OU=IT,OU=US,DC=DOMAIN,DC=COM
CN=user3,OU=IT,OU=US,DC=DOMAIN,DC=COM
CN=user4,OU=IT,OU=US,DC=DOMAIN,DC=COM
You can use OU=IT,OU=US,DC=DOMAIN,DC=COM as Search DN for the Users.
b. example output
CN=user1,OU=IT,OU=US,DC=DOMAIN,DC=COM
CN=user2,OU=IT,OU=EN,DC=DOMAIN,DC=COM
CN=user3,OU=IT,OU=AP,DC=DOMAIN,DC=COM
CN=user4,OU=IT,OU=EM,DC=DOMAIN,DC=COM
You must use DC=DOMAIN,DC=COM as Search DN for the Users, because all users are in different structure under the root of the domain.
c. example output
CN=user1,OU=US,OU=IT,DC=DOMAIN,DC=COM
CN=user2,OU=EN,OU=IT,DC=DOMAIN,DC=COM
CN=user3,OU=AP,OU=IT,DC=DOMAIN,DC=COM
CN=user4,OU=EN,OU=IT,DC=DOMAIN,DC=COM
You can use OU=IT,DC=DOMAIN,DC=COM because this is most top OU under which all structure below are located.
The concept is to read from right which is the top structure, to the left and found a matching OU= under which all users are located.
Is is recommended to run this command for every group you want to use in RSSO for Authentication and Authorization
You should take a look to all groups you want to in the TrueSight Products.
The easiest way might be to use the root of the domain DC=DOMAIN:DC=COM for the search DN, but for security and performance reasons this is not recommended.
2. Find the best Group Search DN, replace groupname with the name of the group.
dsquery group -name groupname
example output
CN=groupname,OU=US,OU=IT,DC=DOMAIN,DC=COM
This output shows the DN from the group, run the command against all groups, and read from right to left to find a Organization Unit level under which the groups are located, it is the same concept as to find the best DN for the users.
3. get details for a single user, could be useful to verify the service account, replace username with the name of the user
dsquery user -samid username | dsget user -fn -n -samid -disabled
example output
dn samid fn disabled
CN=username,CN=Users,DC=domain,DC=com username username no
To test the LDAP integration with TSPS
Login with wit
h Admin user to TSPS( admin with admin12345 password is default)
Use the Burger icon in the top upper left corner and go to Administration Authorization Profiles, use the Burger Icon before the Profile Name to select Edit
Use the Burger Icon at one of the Profiles at the right side and select Edit.
Click on Add Group, this should show the Active Directory Groups, if no Active Directory tools are listed you can check the RSSO logs for errors.
But try to do a search with the prefix of the group, for example if all groups start with TSCO search for TS*, if the groups are listed after this search.
It is iliekly that the result of the ldap search exceed the limit configured in Active Directory and you need proper group filter.
Error example messages from rsso.0.log
SEVERE Thread_41 com.bmc.rsso.admin.helpers.LDAPHelper.isLDAPServerAccessible(): LDAP connection error
ERROR: [LDAP: error code 49 - 80090308: LdapErr: DSID-0C09042F, comment: AcceptSecurityContext error, data 52e, v2580]
The data 52e error does typically mean that account used as Bind DN and the password is not working.
Check if the correct password is used,Please also check if the DistinguishName used is correct
A 3rd Party LDAP Explorer could be used to verify the account by trying to connect to Active Directory.
Check with Active Directory Administrator for the correct DistinguishedName and password
SEVERE Thread_46 com.bmc.rsso.admin.helpers.LDAPHelper.isLDAPServerAccessible(): LDAP connection error
ERROR: [LDAP: error code 49 - 80090308: LdapErr: DSID-0C09042F, comment: AcceptSecurityContext error, data 533, v2580]
The data 533 error does typically mean that the account is Disabled or Locked out, due to too many password attempts in Active Directory.
Check with the Active Directory Administrator if the account is disabled or locked out.
A 3rd Party LDAP Explorer could be used to verify the account by trying to connect to Active Directory.
INFO Thread_42 com.bmc.rsso.admin.helpers.LDAPHelper.isLDAPServerAccessible(): Checking server:port - hostname.domain.com:636
SEVERE Thread_42 com.bmc.rsso.admin.helpers.LDAPHelper.isLDAPServerAccessible(): LDAP connection error
ERROR: hostname.domain.com:636; socket closed
Check if the ""The Use TLS connection" is enabled", the connection is against a LDAPS Port, this connection requires a certificate from the domain controller
or the certificate authority signed the certificates. See keytool example for more details.
INFO Thread_65 com.bmc.rsso.admin.helpers.LDAPHelper.isLDAPServerAccessible(): Checking server:port - hostname.domain.com:636
SEVERE Thread_65 com.bmc.rsso.admin.helpers.LDAPHelper.isLDAPServerAccessible(): LDAP connection error
ERROR: simple bind failed: hostname.domain.com:636
com.sun.jndi.ldap.LdapClient.authenticate(LdapClient.java:219)
com.sun.jndi.ldap.LdapCtx.connect(LdapCtx.java:2788)
A connect against LDAPS Port and the TLS Option is selected, but you need to import the certificate from the certificate authority which signs the certificates from
the domain controller. See keytool example for more details